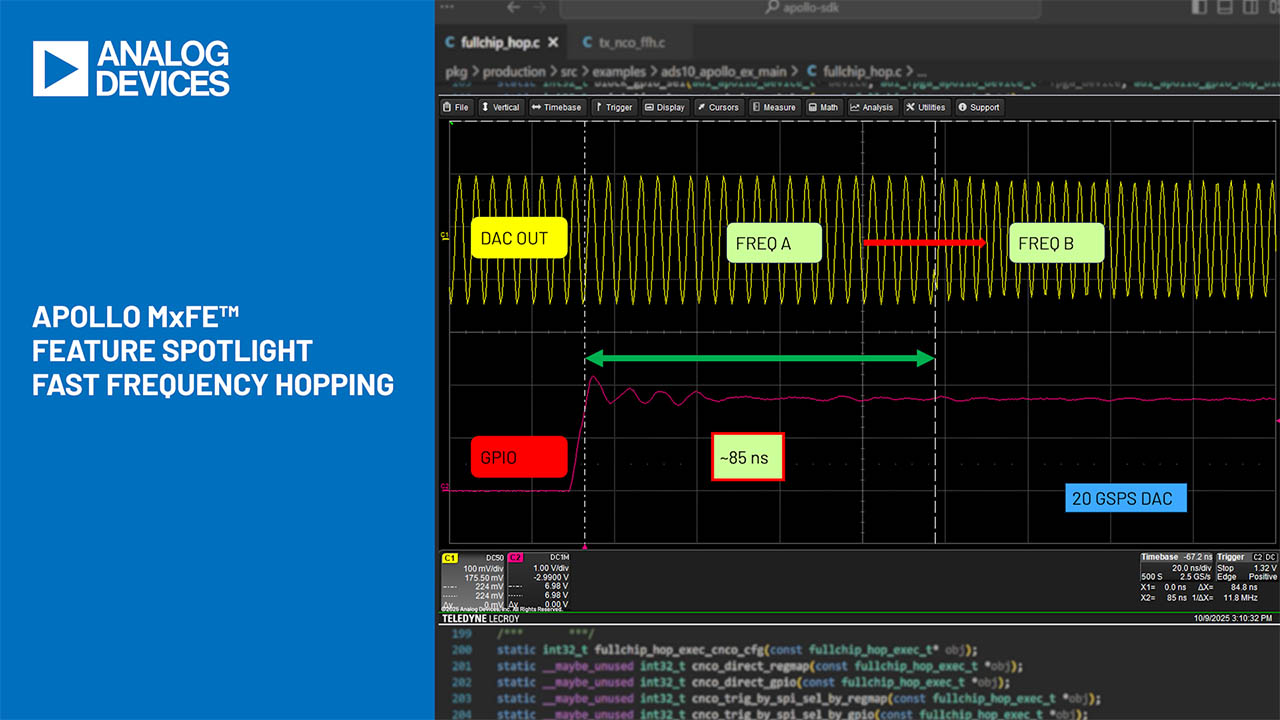
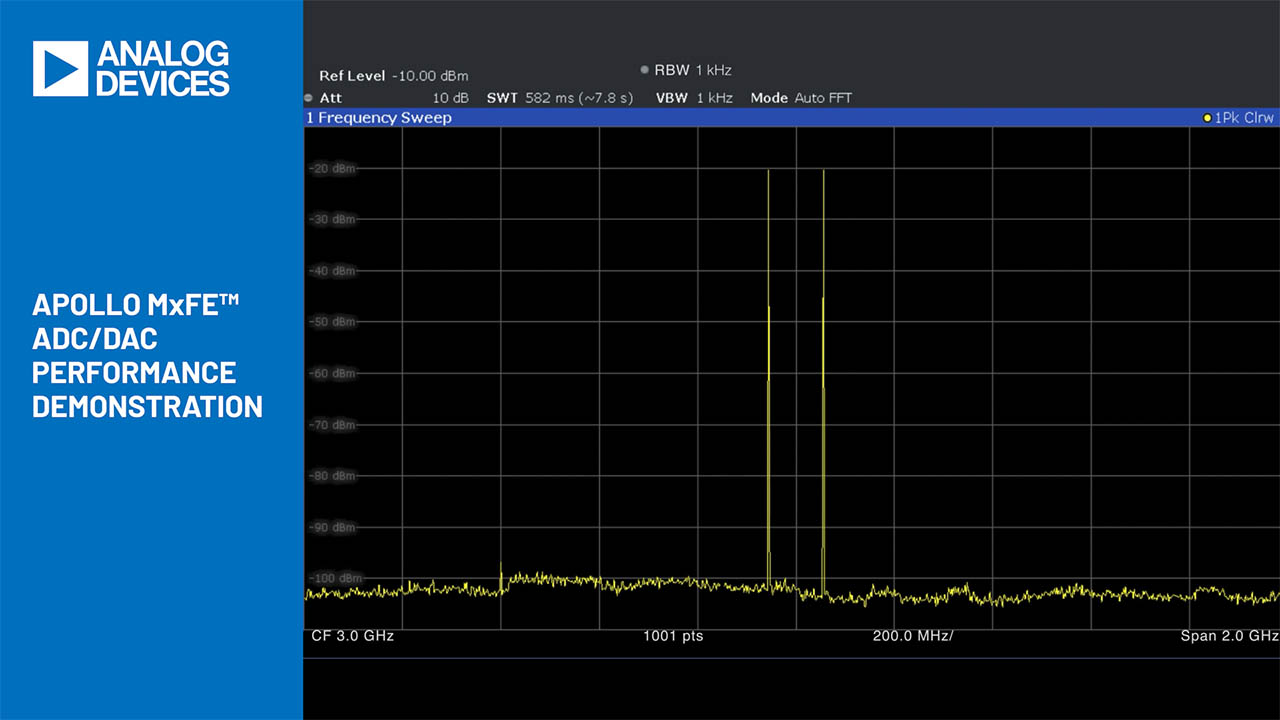
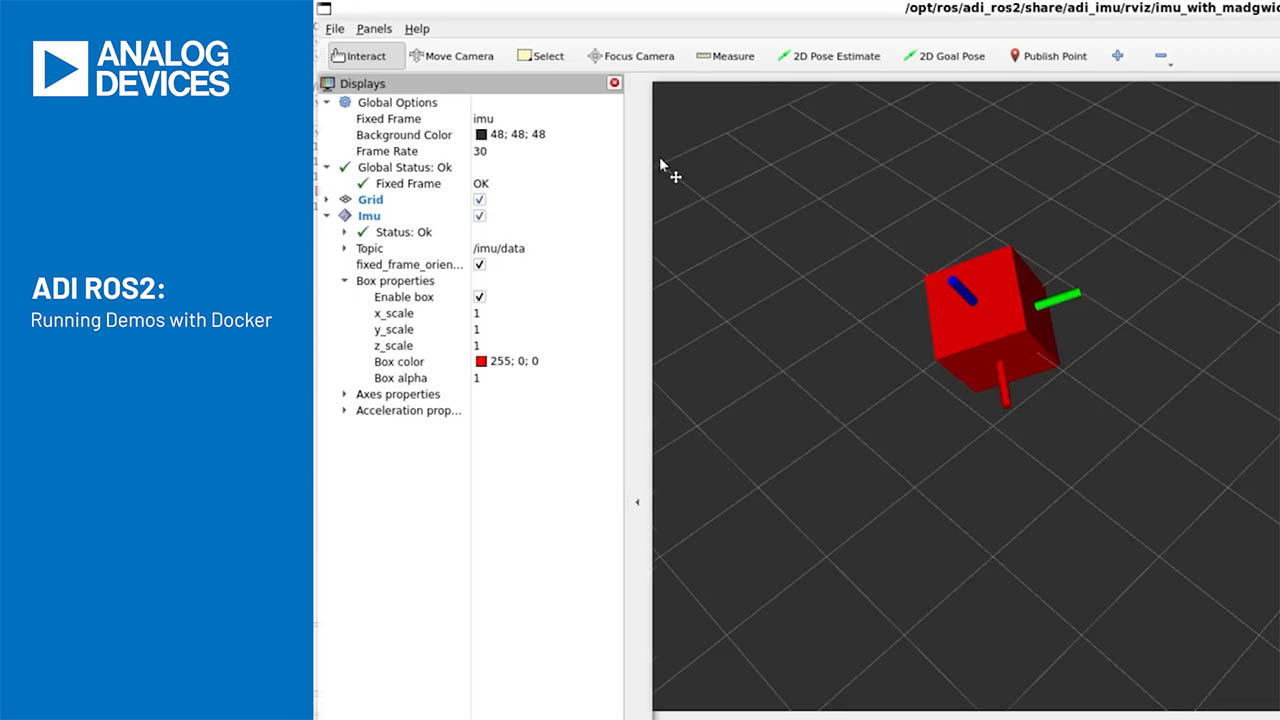
Why Now is a Good Time to Secure Your Embedded Systems with SHA-3
Abstract
Published by the National Institute of Standards and Technology (NIST), Secure Hash Algorithms continue to evolve to provide increasingly stronger levels of cryptography-based security. The latest iteration, SHA-3, has a new internal computational structure as compared to previous NIST-specified hash algorithms to address known vulnerabilities of its predecessors. As embedded systems become smarter and more connected, it’s more critical than ever to safeguard them from attack. SHA-3 can help; however, implementing cryptographic hash functions can be challenging without a background in cryptography. This white paper discusses the merits of SHA-3 and highlights how secure authenticators designed with SHA-3 algorithms and physically unclonable function (PUF) technology can provide strong embedded security without requiring cryptography expertise. Read full article.
Related to this Article
Products
PRODUCTION
Two Channel, 5kVRMS I2C Isolator
PRODUCTION
DeepCover Secure Authenticator