AN-2586:提升用户信心,确保电动汽车电池纯正可靠
引言
汽车电气化趋势已势不可挡。这一变革将有助于减少污染和化石燃料的消耗,为环境保护和可持续发展带来显著的好处。当前的技术进步正在加速电气化进程。如今的电动汽车在一次充电后的续航里程已可媲美加满油的传统内燃机汽车,同时在加速性能方面也毫不逊色,甚至更胜一筹。全球每年生产约 1 亿辆新车,锂离子电池的应用达到了空前的规模。电动汽车(EV)制造商将因此面临一系列新的挑战,而妥善应对这些挑战已成为行业的当务之急。首先,安全始终是首要考量,这不仅关乎车内人员,对行人和其他车辆中的人员也同样重要。其次,随着使用寿命有限的车用电池的大规模部署,必须关注可持续能源和环境问题。最后,电动汽车电池是高价值部件,更换成本高昂。这可能会诱发盗窃行为,催生被盗电池的黑市交易。如果汽车原始设备制造商(OEM)对这三个问题处理不慎,不仅会造成自身品牌声誉受损,而且正品 OEM 更换电池的销售收入也会流失。电动汽车电池的安全认证可以帮助解决这些问题。ADI 公司还提供有线电池管理系统(BMS)拓扑解决方案。本应用笔记重点关注有线BMS应用,并详细介绍能够增强电动汽车电池安全性的汽车安全认证器。
如果您希望结合线电池管理系统(wBMS)解决方案 实现电池认证功能,请联系 ADI 公司代表。配 备 DS28C40 等认证器的电池模组可从源头确保安全 。
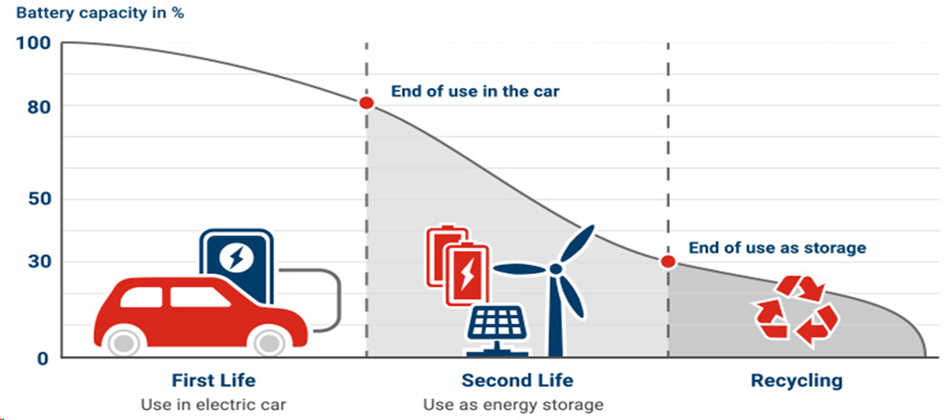
安全与防护往往相互依存。就汽车而言,如果关键系统的安全性得不到保障,车辆的整体安全性就可能被削弱。以锂离子电池为例,产品制造缺陷可能引发火灾和爆炸 1。与 OEM 认证产品相比,未经授权的制造商所生产的电池价格可能较低,但在结构用料和安全检测方面往往不达标。大多数电池虽不至于引起火灾,但性能下降可能间接损害 OEM 的品牌声誉。正品电池在汽车中结束使用寿命后,通常仍具备“第二次生命”的潜力,可重新部署于固定式储能中心。为了防止正品 OEM 电池被重新用于其他车辆,应通过不可逆的报废程序将其退役。数字认证技术让汽车能够识别所连接电池的真伪,确保仅使用正品电池,拒绝假冒产品。ADI 公司的 DS28C40 和 DS28E40 认证器就属于此类设备,不仅提供认证功能,还能将电池使用记录安全存放在存储器中,实现可追溯性。制造信息、服务信息和退役状态等关键信息,可以轻松存储在由认证器数字签名的安全一次性可编程(OTP)存储器中。
随着锂离子电池逐渐老化,其单次充电所能储存的能量及可提供的峰值电流都会下降,导致电动汽车续航里程缩短和整体性能下降。每年有数千万至数亿的电池包退役,二次利用是提升能源可持续性的重要途径 2。固定式储能中心能够非常有效地储存能源,并且平抑风能、太阳能等波动性较大的可再生能源的电力输出。退役的电动汽车电池非常适合重新部署到这些固定式储能中心。可追溯性依然重要,不仅要记录电池加入储能中心的时间,还要追踪电池的各项性能指标。
如今,大多数电动汽车电池包难以拆卸,因此并非盗窃的主要目标。另一方面,一些 OEM 提出了轻松更换电池包的策略 3:建立一个配备预充电电池包和专用电池包存取设备的换电站体系,让驾驶员能在极短时间内完成补能,比现有燃油车(ICE)加油还要迅捷。由于电动汽车电池价值高昂,这种做法无疑容易招来窃贼。通过身份验证器将电池与特定车辆绑定,可以有效防止窃贼将电池从原车拆下后,再安装到其他车辆上。为实现这一机制,授权换电站在日常电池更换操作中,必须能够连接到电池电子控制单元(ECU),并启动与授权电池的配对过程。服务站设备可能需要通过云连接,为汽车 OEM 提供合法配对操作记录的审计路径。这种方法所需的基础设施相当庞大。因此,倡导换电策略的 OEM 是否会继续推进实施,仍有待观察。
实施电动汽车电池认证
质询-响应身份验证的优势
上文探讨了电动汽车电池认证和退役处理的不同动因,包括防止电池在未经授权的情况下再次用于电动汽车。接下来,我们将明确提出一种足够强大的实施方案,以真正确保用户安全和车辆性能,同时保护汽车 OEM 的经济利益和品牌声誉。
一些看似直观的方法,例如通过序列号追踪或将数据存储在无安全防护的存储器中,往往容易被攻破,缺乏足够的安全强度:一名具备中等技术水平并使用低成本设备的黑客,一般在半天时间内就能绕过此类安全措施。身份验证方法的强度应与所需应对的挑战相匹配。强身份验证需要借助加密手段。对于许多应用而言,质询-响应认证已被证明是验证设备或备件身份的首选技术。
采用对称和非对称方案的质询-响应身份验证
质询-响应认证必须以强健的算法作为支撑。ADI 公司的 DS2478、DS28C40 和 DS28E40 支持以下算法:
- 安全哈希算法(SHA),它基于汽车 BMS 和电芯之间的共享密钥,是一种对称方案。
- 基于椭圆曲线数字签名算法(ECDSA)的非对称方案,它在模组中使用私钥,在汽车侧 BMS上使用公钥。
ECDSA 和 SHA 算法被密码专家公认为安全性较高的算法,并已由美国国家标准与技术研究院(NIST)实现标准化。
DS2478、DS28C40 和 DS28E40 均符合汽车 AEC-Q100 标准,专为子系统或备件认证而设计。它们支持认证所需的基本特性,避免了市面上解决方案的功能堆砌和过度设计。
这些安全 IC 中的硬件加速器支持 SHA-256 和 ECDSA 计算。
现在,我们来探讨对称和非对称认证方法的优点与局限性。
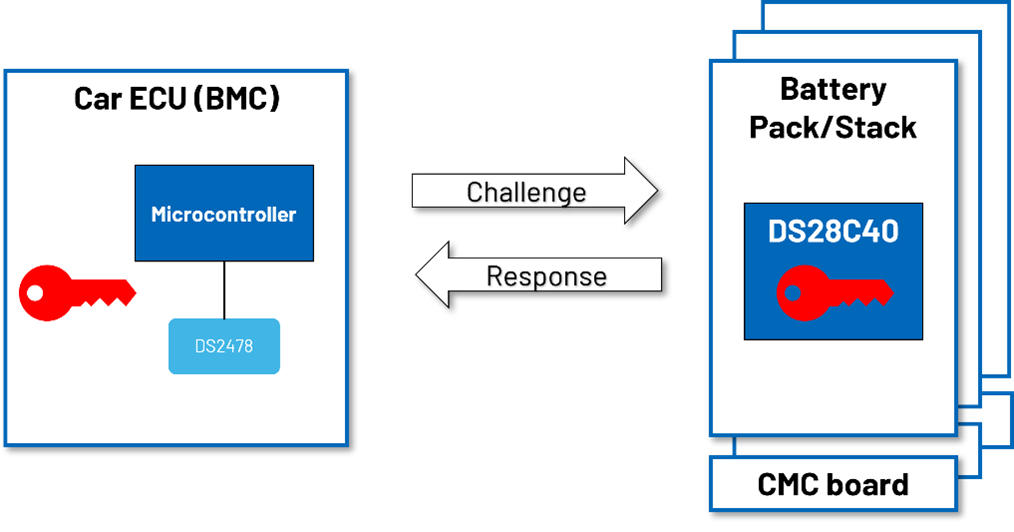
基于 SHA-256 的对称方案的主要优点是性能。虽然 SHA-256 是一种高安全性算法,但其复杂度适中。因此,它计算速度很快,运行一个模组的质询-响应认证大约需要 5ms。
该方案要求特定汽车和车上所有电池模组共享同一密钥。
安装此类共享密钥的一种可能方法如下:
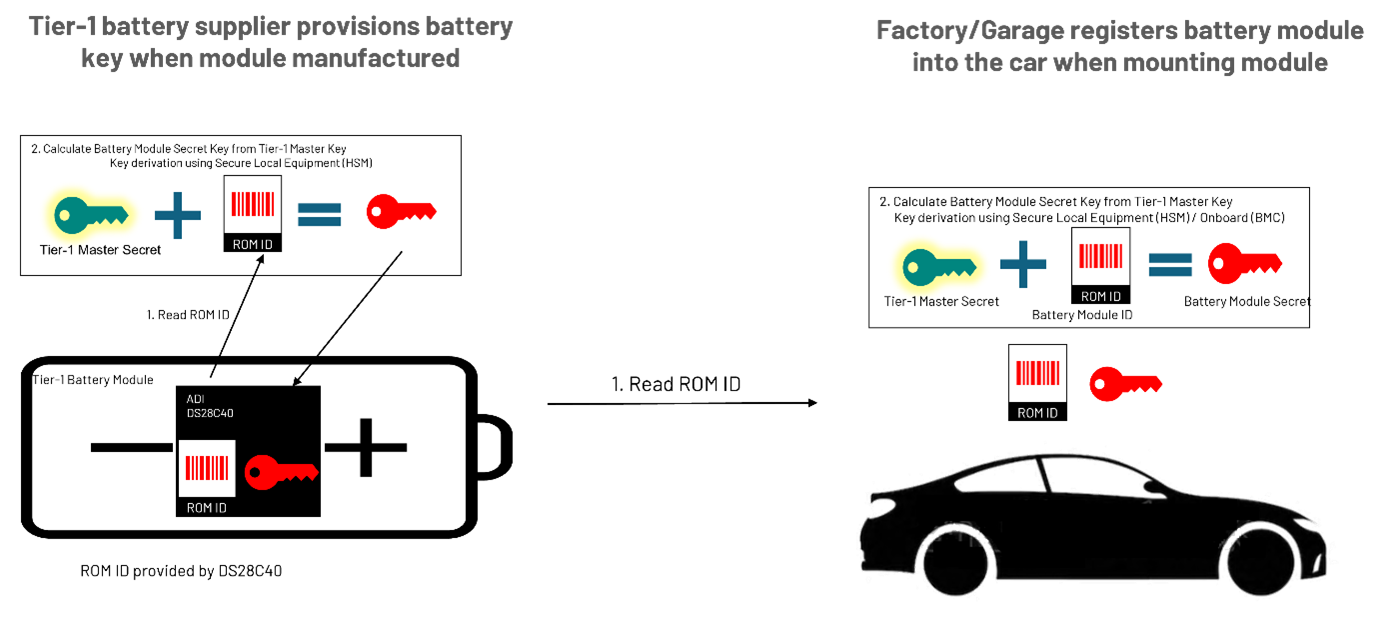
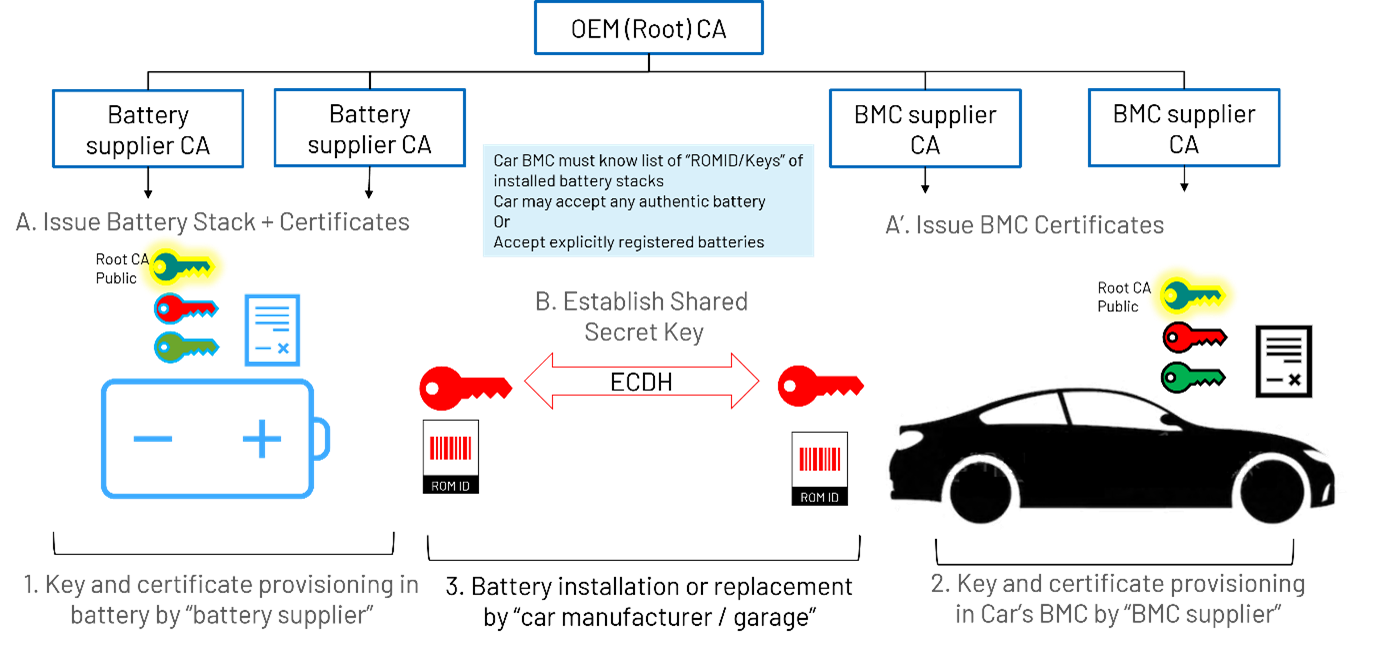
电池供应商和 OEM(以及授权维修机构)最初共享一个主密钥。
利用 DS28C40 或 DS28E40 提供的唯一 ID 和该主密钥,一端的电池供应商和另一端的安装机构为特定模组计算出唯一的派生共享密钥。所述派生密钥采用 SHA-256 算法来计算。此计算由电池模组侧的 DS28C40/DS28E40 执行,也可由汽车/电池管理侧的 DS2478 执行。
挑战在于,一级主密钥必须始终受到保护。为此,往往需要在供应链的各个环节设立安全设施,但这样做不仅实施难度大,而且成本高昂。ADI 公司可以代表 OEM 或一级客户设置主密钥,从而免除他们保护设施物理安全的负担,并克服对称加密方法的一个主要弱点。
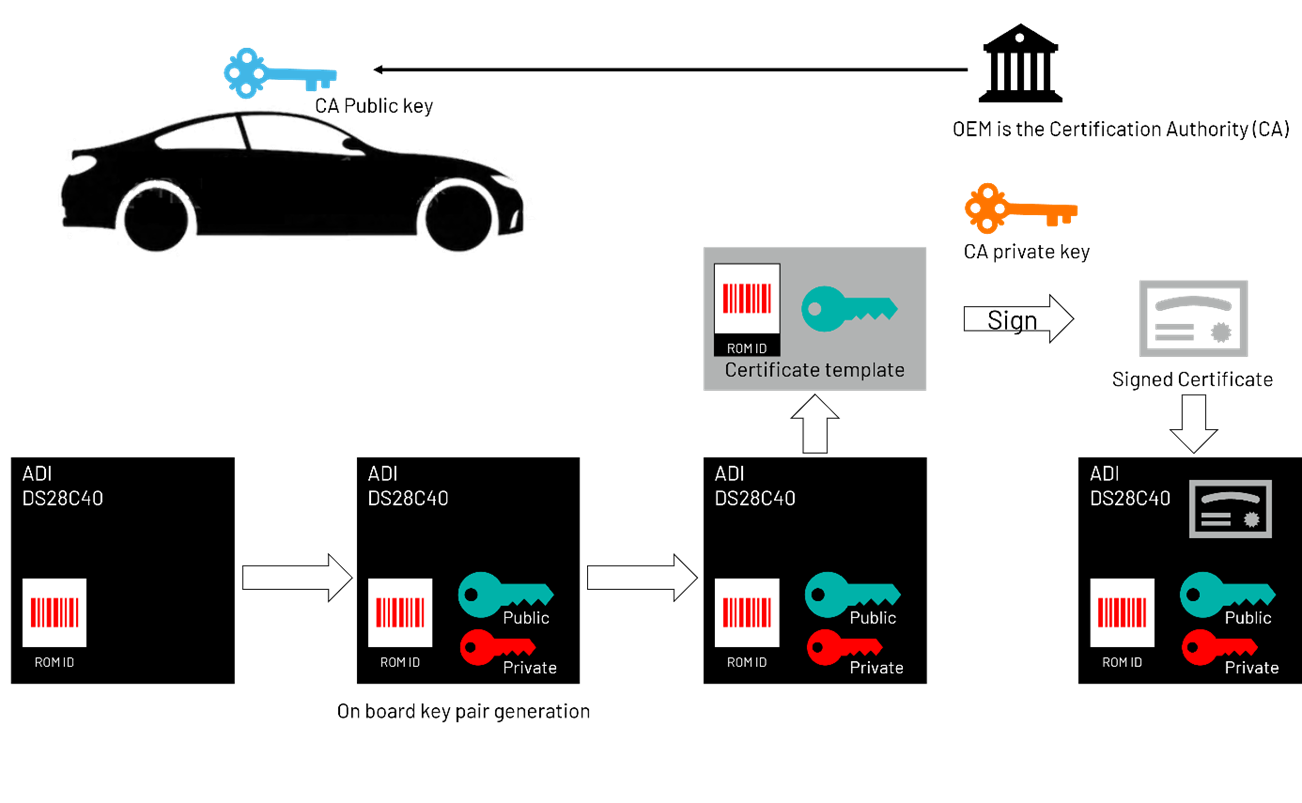
另一方面,基于 ECDSA 的非对称认证方案的主要优点是避免了共享密钥。此外,基于证书的方案支持每个电池模组实现唯一密钥对。
该方案的一个主要优点是,模组可以凭借其独有的私钥进行认证,该私钥始终驻留在 DS28C40 或DS28E40 的安全存储器中。显然,相较于共享密钥方案,私钥遭到泄露的风险要低得多。唯一需要设施安全防护的环节是认证机构使用其私钥对证书进行签名的操作。此环节可由 OEM 或电池供应商使用所谓的硬件安全模块,通过合理的投入来完成,而无需为整个设施提供物理安全防护。密钥对生成和证书签名也可以委托给 ADI 公司,OEM 或电池供应商收到的器件可直接集成,无需额外配置。
但在享受这种灵活性的同时,也要付出一定的代价:每次电池认证,都需要运行两次 ECDSA 验证操作,导致认证执行时间延长。在模组以菊花链方式连接的配置中,每次引擎启动都需要较长的认证时间,因此这种方案的实用性大打折扣。
为了克服这一缺点,同时仍然保留基于 SHA-256 的认证的优势及性能,配置共享密钥的一种替代方法是利用 DS28C40 的非对称加密能力:DS28C40 支持椭圆曲线 Diffie-Hellman (ECDH)算法。该算法支持为两个相互认证的实体计算一个共享密钥。
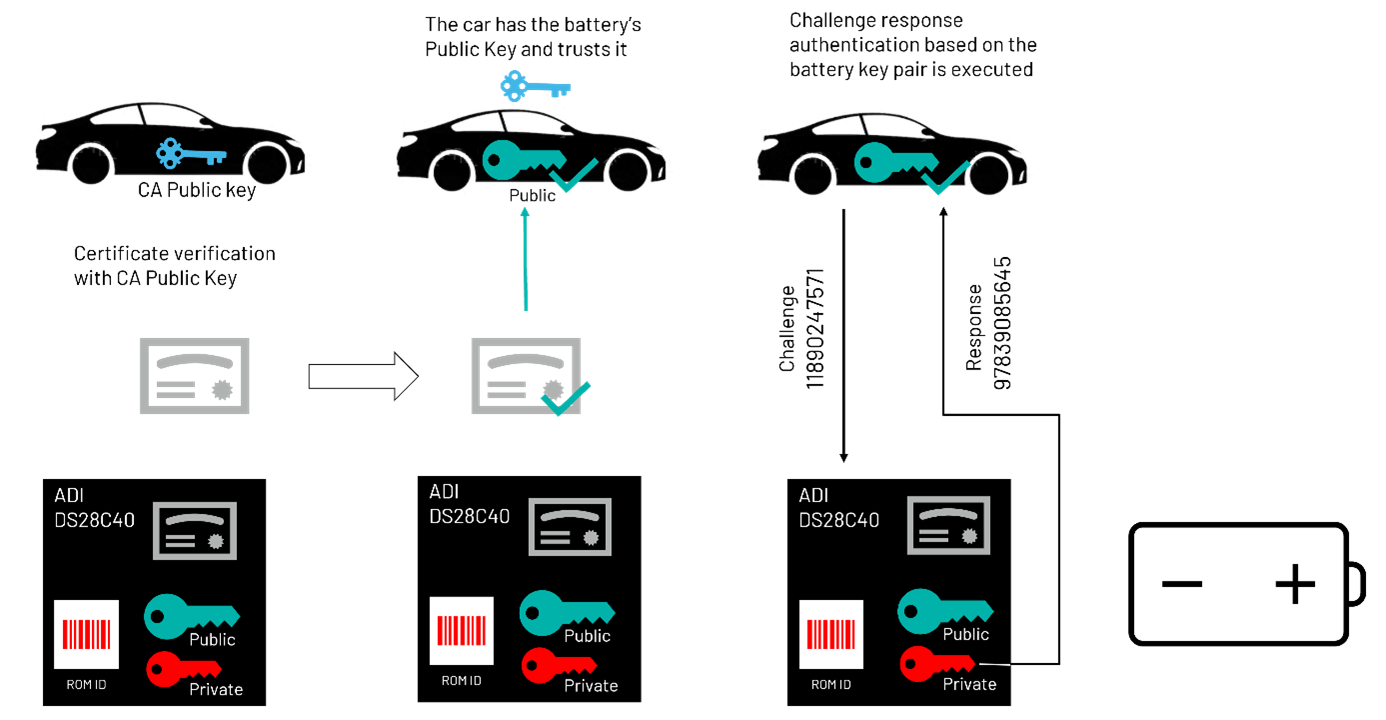
在此方案中,密钥和证书分别安装在电池和车辆中。证书受相关认证机构的信任。认证过程可能涉及多家电池供应商的认证机构及多家电池管理控制器一级供应商。
安装时,在汽车和电池模组进行 ECDSA 相互认证之后,使用 ECDH 算法在汽车电池管理控制器(BMC)和电池模组上计算共享密钥。计算发生在 BMC 侧的 DS2478 上及电池模组侧的 DS28C40/DS28E40 上,得到的共享密钥存储在 DS28C40 或 DS28E40 的安全存储器中。每次需要认证操作时,可以使用共享密钥运行 HMAC/SHA-256 身份验证。耗时的非对称认证和共享密钥计算只需在安装期间进行一次,电池认证期间性能不受影响。这样既能在汽车启动时发挥 SHA-256 的性能优势,又能确保密钥在整个供应链中不会被泄露。
得益于非对称加密和证书的灵活性,上述方案可以适应更复杂的供应链组织。有关所有可能版本的更多信息,请联系 ADI 公司代表。
公钥证书存储使汽车 OEM 能够:
- 利用现有公钥基础设施(PKI)来管理 OEM 和一级供应商密钥。
- 实现车辆与电池模组的配对。
安全存储器可以存储和保护敏感数据,例如可追溯性信息、制造数据和生命周期信息。
与 ADI 电池管理系统相结合
有线电池管理系统
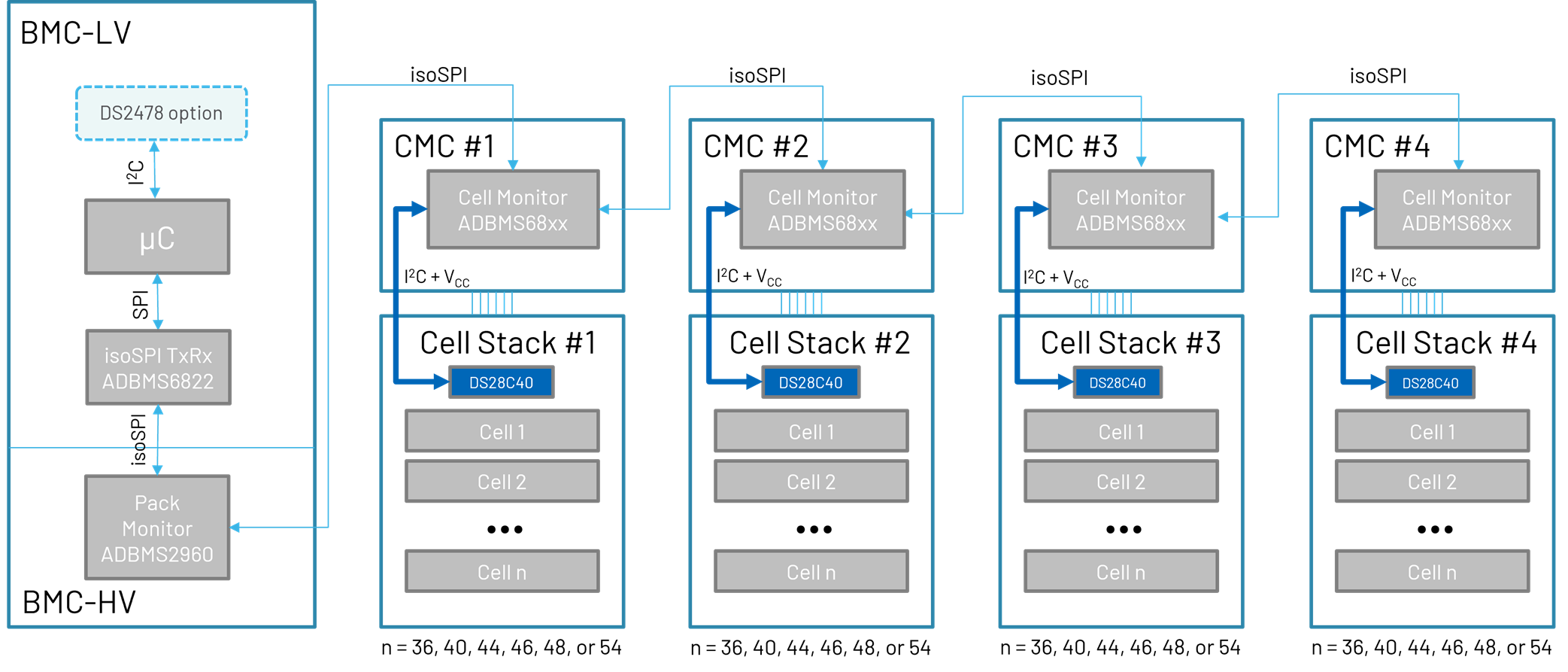
在 ADI 有线 BMS 中,电池管理控制器通过 ISO SPI 与电池模组通信。ISO SPI 协议允许两个隔离器件进行串行外设接口(SPI)通信。ISO SPI 具有 I2C 隧道能力,支持与 DS28C40 连接,如图 9所示。通过这种通信媒介,BMC 可以单独验证每个电池模组的身份。有关 ISO SPI 的更多信息,请参阅本文。
无线电池管理系统
虽然 ADI 公司的 。wBMS 解决方案具有内置安全性,但对电池模组本身进行身份验证仍然有意义。如果您对此类解决方案感兴趣,请联系 ADI 公司销售代表。
使用安全认证器进行退役处理
正如本应用笔记第一部分所述,将退役的电动汽车电池重新部署于固定式储能中心,是应对未来环境挑战的重要举措。
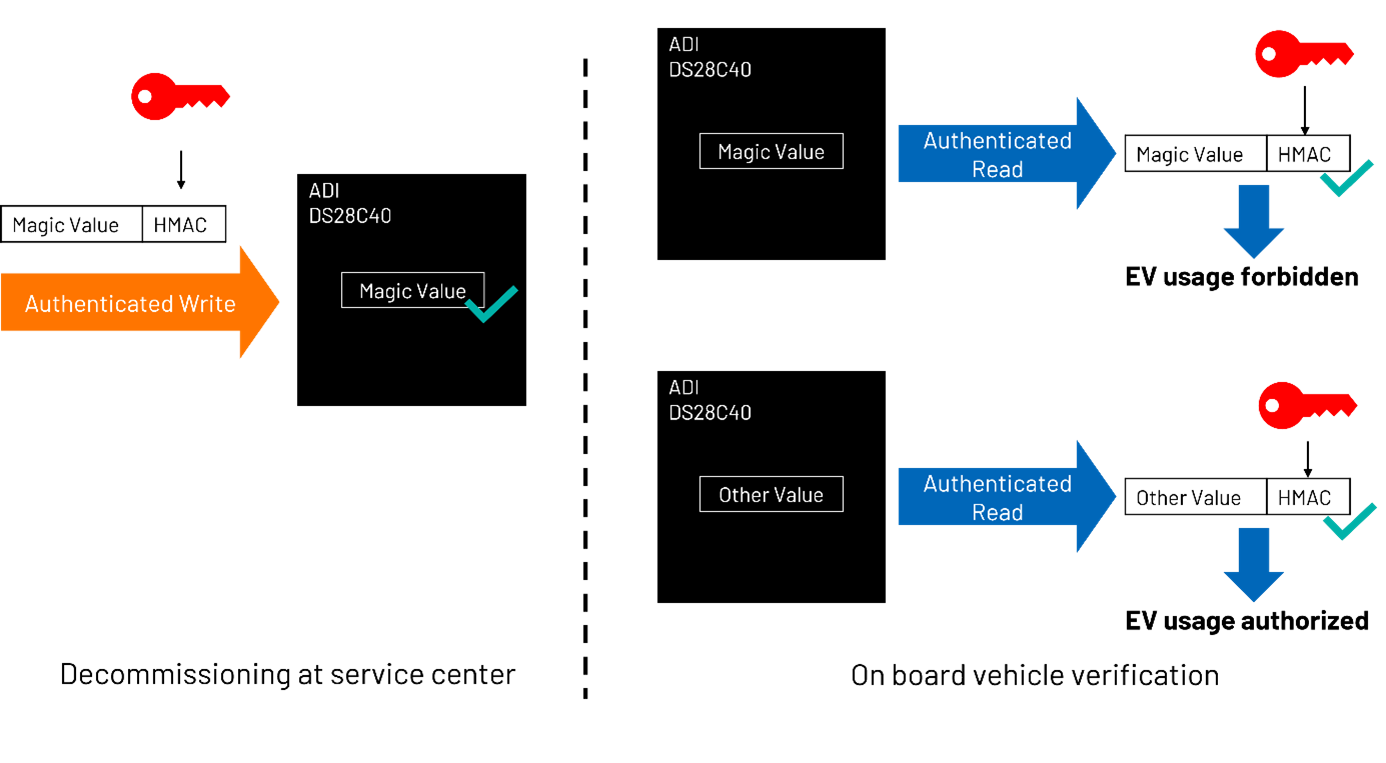
为此,必须确保这些退役电池在其性能已不符合电动汽车要求后,不再重复用于其他车辆。也就是说,应以安全且不可逆的方式对电动汽车电池模组进行退役处理。除了电池模组认证之外,DS28C40、DS28E40 和 DS2478 还支持安全退役。一个很直观的想法是:我们可以在电池模组附加的芯片中存储一个“魔法值”(即任意已知的预设值),利用它来判断电池模组是否仍可用于电动汽车,还是已经退役。这种简单方法只有在满足以下条件时才有意义:
- 未经授权的实体无法更改存储器内容。
- 从存储器中读出的值是可信的,并且在读取时不会被修改。
否则,攻击者只需在编程或读取阶段更改存储器内容,便可轻松破坏该机制,重新启用本应退役的电池模组。
DS28C40 或 DS28E40 及可选配的 DS2478 提供了确保存储器内容可信的机制。6kb 板载一次性可编程存储器(OTP)的用户页面保护设置可能根据需求进行自定义。更具体地说,通过将保护设置为“认证写入”,可以防止未经授权写入页面。
为了对写入操作进行认证,有效载荷数据会附加哈希消息认证码(HMAC)。HMAC 是有效载荷数据和共享密钥的函数。得益于 SHA-256 的数学特性,不知道密钥就无法伪造 HMAC。这样就可以确保,只有车辆的 BMC 或授权服务中心才被允许对存储魔法值的存储器页面进行编程。一旦魔法值被写入板载芯片存储器中,攻击者就无法修改它。
读取存储器内容时,DS28C40 或 DS28E40 也会根据 IC 中存储的密钥附加 HMAC,从而保证从存储器中读取的值是可信的。同样,由于攻击者不知道共享密钥,因此无法替换从存储器中提取的值。
结语
ADI 公司为各类垂直市场和应用提供身份验证解决方案已有逾 35 年历史。ADI 公司的成熟技术能够保障医疗配件和耗材的安全,防止患者使用劣质产品,从而有效守护患者的健康与安全。这些技术现在可用来应对电动汽车和环境保护面临的重大挑战。
借助 ADI 公司的安全认证器,开发者能够实现强加密保护,而无需依赖复杂或过度设计且昂贵的解决方案。
参考电路
1. Lithium-ion battery fires are happening more often. Here's how to prevent them | CNN Business
2. Electric vehicles, second life batteries, and their effect on the power sector | McKinsey
3. Innovative Smart Power Service Solution